Rev. 0
** Warning **
This is a very lengthy topic directed toward the need for support in removal of a very complicated malware infestation/hack. To help avoid any confusion and assist readers when searching for similar issues, I have broken the post up into sections which are accessible via the drop-down style menus as advised by by the Ubuntu-Mate Community administration prior to writing this post. I would also like to take a moment to say thank you for the help received thus far and for continued assistance, as this type of topic extends beyond the normal boundaries of support offered by this forum. I hope my search for a solution with this problem ends here. I will try to keep a revision log at the end of the post for any changes I make, indicating the current revision level at the begginging of the post.
Problem:
I am currently running Ubuntu-Mate 19.04 which is heavily infected with malware. I also several other devices infected with the same or similar malware/installed back-doors. This malware is undetectable by traditional anti-virus engines and irremovable by low-level storage device wiping techniques and replacing equipment. I suspect the malware to be located in the firmware of the mother board or possibly other components, such as third party graphics cards, networking adapters, routers, modem, keyboard, etc. but lack the tool-sets and training to thoroughly understand and deal with the issue myself. The malware presence is seen in Ubuntu-Mate among other operating systems. The malware exhibits characteristics of a hypervisor rootkit, worm, and Trojans. I have been battling this problem and looking for help for 2.5 years now after being turned away by some of the biggest names in the anti-malware industry and Microsoft (while using Windows 10) after extensively working with their support teams for up to five month depending on the company.
System Specs & Equipment List
I have (7) PC's (one is a laptop, four are Intel architecture and three are AMD), (1) Raspberry Pie, (2) Android Tablets and (2) Android Smart Phones which are all infected. The PC I am using as an example for this post is listed below. The networking equipment I have consists of (4) cable modems, (8) routers and (2) switches (only one of each in service). I have one printer which does have networking capabilities and up-gradable firmware. I have three smart TV's two of which I highly suspect infection. If additional details are needed on the equipment mentioned, I will provide it upon request.
Dell Optiplex 7010
Processor: Intel(R) Core(TM) i5-3470 CPU @ 3.20GHz
RAM: 8Gb DDR3
Storage: 500Gb HDD, Western Digital Blue
Keyboard/Mouse Combo: Logitech K120 (wired)
Monitor: HP VH240a
Network Adapter: On-board
Graphics Adapter: On-board
Optical Drive: OEM Stock drive
Detailed System Specifications can be found at my PasteBin via the link below.
https://pastebin.com/u/dmabe
Detailed History
In January, 2017, the computer I had at the time was getting old and outdated, so I decided to spring for an upgrade. The upgrade was one where I ordered parts and planned on assembling myself. After placing the order, I decided to start looking for some software that I wanted, namely, Blu-Ray burning software.
As temping as it was to find a pirated version, I decided that may not be the best idea and started looking for a trial sample I could evaluate. After some searching, I found one to try and downloaded it. When I ran the executable file I had downloaded the trouble began.
Up to that point in time, I had been familiar with some types of malware having dealt with a couple virus infections in the past and wasn't too concerned with the events that were taking place due to the malware I had inadvertently just installed on my old PC. Even if I was not able to remove the malware, I wasn't concerned because the parts for the new PC were on the way.
During the same time frame, I began to notice abnormalities with my mobile phone. It didn't take lone before I suspected that it had been hacked and what was transpiring was due to the the presence of another (simultaneous) user. Not quite sure how to deal with the situation, I bluntly approached the user by typing a message in the text box, not hitting send. When I received a reply, my suspicions were confirmed.
There was some crude back-and-forth communication, continuing for nearly a week and a half before i was eventually served with an ultimatum to follow some obscure directions, which i answered promptly and rudely. Shortly after, I heard sounds being emitted from two of my smart televisions, resembling what can only be described as catastrophic electronic failure, leaving one of the two TV's inoperable for approximately one week after. I am still unsure what was done to the televisions but suspect it was to allow for an OTA hack, similar to the Samsung smart TV hack discovered in 2017. However, both televisions of mine which were affected are Sony Bravia televisions and it is unknown to me if they are even susceptible to such a hack. I presume they are.
When the parts for my new PC arrived, I knew I would have to isolate it from the any of the older parts and did my best to do that but after finalizing the change over with my ISP and new modem, I fired up the new machine and instantly, it behaved as if it were under the control of someone/something other than me and never behaved much differently there after. I would like to make a note here that the most dramatic of oddities I saw from the new PC at that time seemed to be coming from the optical drive, which is one of the components I still see as being one of the most affected components still.
To clarify what I had purchased when replacing equipment initially, included a new PC wireless keyboard/mouse combo, monitors, web-cam, modem, router, NAS, printer and PC stereo/speaker system*. The only IoT devices that remained in service at the time I made the PC switch were my home stereo receiver, two smart televisions, hand-held GPS, Bluetooth capable heart-rate monitor/exercise bike, Blu-Ray player, Bluetooth ear bud and mobile smart phones. The only devices which had shown any signs of infection were the televisions and the phones but none of the devices were connected in any kind of network at the time the new PC was commissioned.
*See the "Equipment Details" section for specific information
Symptoms
The symptoms associated with the malware have dramatically varried over the timeframe of infection, almost to the point, that it felt as if I were a test sample or this was a trial run for the malware designers. I have used various AV programs which have detected malware in the form of adware, trojans, rootkits, ransomware and worms. Very few AV engines will actually provided detections at all. ClamAV will reliably and consistently provide detections after initial OS installation and there after but no AV I have tired to date has removed the root cause of this problem and I have tried most every major vendors version and others.
After OS reinstallation, it takes some time for the malware to really begin to be noticeabe, which may be in part that there isn't "malware" initially installed but something else taking place similiar to DNS poisloning, where later down the road, I am unknowingly downloading and installing the malware from spoofed/redirected webpages.
What is deffinately noticeable is what is being displayed on the command line during the installation, the info on the command line seen during post and the log files, showing those and several other error messages.
Other notable symptoms which are not always present are increased network traffic, disfucntional applications, malware detections, spoofed webpages, abnormal networking configurations, use of virtualization when virtualization shouldn't be present, presence of logical drives/partitions without my creation or instruction to do so, partion changes and many other.
There is an extreme amount of deception at work with this malware as well as high levels of Bluetooth activity, and nearfield communication if the capability with the hardware permits. The malware exhibits behavior as if it is on a timer but does not follow a set schedule and seems to be most active in the evening through the night until approximately 6 a.m. MST.
Although I cant describe in detail I have seen in the past several indications that there is a direct tie/connection with the phones and the computers but cant factually comment too much more on this without it being considered speculation.
The most notable symptoms I see that indicate this malware may have infected the firmware is after turning off my PC or hard resetting the computer, all but the laptop will imediatly turn back on for a brief moment and then turn back off; this happens approximately 95% of the time and the other 5% it doesn't but for unknown reasons. I have seen changes such as the date and time, missing attributes and other altered values/data in the BIOS. When using Windows 10 pro, I have received error messages stating the the TPM is in a timeout period, from defending against dictionary attacks, and with Linux, there are errors reported during post that include TPM errors/bugs, ACPI errors/bugs, tainted kernels or lack thereof in conjunction with kernel panic and booting issues, spoofed OS windows and complete deny of service/use when there is absolutely no rhyme or reason for lost of permissions to perform those given tasks or functions. I have provided a few examples which can be seen by following the link below to my paste bin, where I've shared the output of a few logs generated by running the fwts-frontend-text, lspci and lsusb applications. The last symptom I will mention for now is believed to be within one of the routers I own as i have been completely denied access to the settings. I tried several methods to re-gain access as per the manufacturers recommended procedures. I momentarily gained access by means of ftps before being denied again and I have not made any more attempts since.
My Efforts of Removal
I'm not even sure where to begin with this section as I have tried nearly everything under the sun I can think of over the past two years but I will try to hightlight the more important efforts in the list below. I have also tried every variation and multiple of each, with similiar attempts made using Windows and FreeDos. I have absolutely no reservations to wipe any of my drives and/or update/downgrade firmware. I am very willing to try anything suggested, even if I have already done it in the past.
Ubuntu-Mate & Other Flavors
- Run scans with ClamAV, RK Hunter, CHKRootKit, Dr. Web, ESET Nod32, Sophos, BitDefender, etc., all done with each PC completely isolated and disconnected from the internet with hardwired, USB mouse and keyboard.
- Run scans as described above but from a protected enviroment or offline by using bootable media generated from a clean computer. Bootable media includes CD/DVD optical drives and USB thumb drives, both of which have been 100% new only being inserted into a clean computer one time before using to try to disinfect my devices. The USB's have included PNY, SanDisk and Kingston make thumb drives.
- Run online scans from AV vendors via their cloud services.
- Storage drive formating and OS re-installation in normal configurations and partitioning schemes, RAID, nework installations, USB thumb drive installs, external storage drive (SSD) installs, etc, both with MBR and GPT formating, utilizing the secureboot and TPM features and also without. The formating techniques/applications used include but not limitted to, fdisk, gdisk, cfdisk, sfdisk, parted, partx, gparted (online and offline), dd, hdparm (trying every available option), remnux, Active KillDisk, Mini Tool Partition Wizard, MBR Wizard and third party hex editing software, manually altering drive sectors.
- Updating/Upgrading/Downgrading/Re-installing drivers, BIOS, ME firmware, monitor firmware, mobile phone firmware, smart TV firmware, storage drive firmware and optical drive firmware.
- I've taken PC's to local repair facilities for repair and also hired professionals to come on site for analysis and repair.
- Sent a motherboard to ASUS for analysis and talked with the engineers of ASUS and Gigabyte regarding firmware infections, possibilities, detection and removal,
- Send a SSD of Samsung make back to the manufacture for analysis and repair
- Worked with AV companies extensively, such as BitDefender, Malwarebytes, Sophos, SpyHunter, RogueKiller, AVG and many others.
- Implemented software based firewalls and also dedicated computers to act as a firewall appliance using Sophos XG
- I have replaced every piece of equipment with the exception of RAM, CPU and power supplies all at once and in intervals, while maintaining isolation to the best of my abilities and knowledge.
- I brought 5 new PC's into this house, having anything that I own with internet capabilites, unplugged or powered off if it coudn't be unpluged and had them become infected within 30-60min of use DONT ASK ME HOW OR TELL ME IT ISN'T POSSIBLE
- I have had the same experiences as listed above but with mobile smart phones. I have flashed ROMs, changed carriers and replaced component in them as well.
- I have tried all the above with all the devices connected too and again with using my phone as a modem to see if it was coming from my ISP, which isn't the case.
- I have attempted to change every password for every online account I could think of that I had at the time. This was interesting becaues I actually lost control 2-3 times with my google account and still see strange things related to google (mainly with the phones but something is also going on with the browsers, where there somehow has a component of Chrome mixed in.....unsure about what is really happening with this, so I'll leave it alone for now.
- I have tried many things not listed here but too many to share. It may be easier if a particular attempt is in question to just ask me and I can tell you if it is something I have tried in the past.
Revision History:
Rev 0 - Original Published Post 7/15/2019


 Wired/Wireless devices ←→
Wired/Wireless devices ←→  (Wi-Fi) Router (w. integrated modem) ←→
(Wi-Fi) Router (w. integrated modem) ←→  Internet
Internet Modem ←→
Modem ←→ 

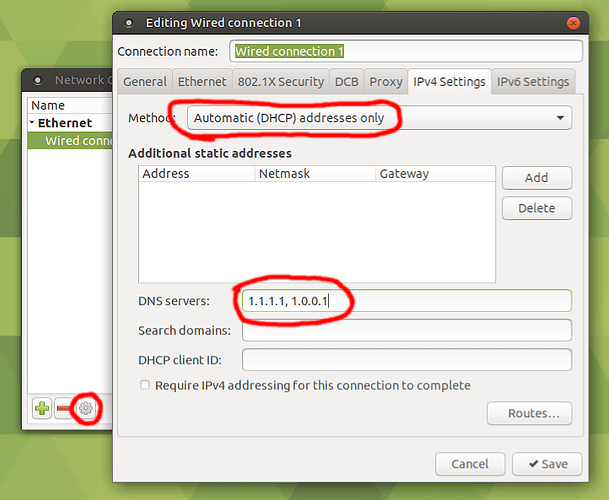
 Here's an example:
Here's an example:
 Software Boutique.
Software Boutique. better this time....LOL? Okay, back to your questions. I did forget to share one other visible problem, which I am taking other measures to find out more about but where it directly relates to this topic and I wanted to include it in the details. Please see the
better this time....LOL? Okay, back to your questions. I did forget to share one other visible problem, which I am taking other measures to find out more about but where it directly relates to this topic and I wanted to include it in the details. Please see the