So I've finally committed to setting up the firewall on my various machines and while it wasn't painless, at least the Gufw graphical firewall program worked and I was able to set up a comprehensive set of rules.
I believe this set of rules can be useful for other users of the community so I've elected to post them here. This may well allow you to avoid some headaches because Gufw has the useful option to load rules from a file.
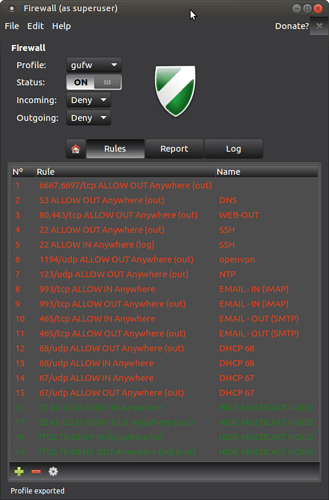
Here's the file in question: [ EDIT: SEE POST #2 ] save it to something.profile then load it from the Firewall application.
Obviously not all of my rules will suit you so I'm gonna explain what each of them do and you'll be able to use the graphical interface to remove those you don't like / use. The rules are not perfect (some might be useless) and I will welcome constructive criticism.
The default rules are set to "deny" which means any packet entering or leaving your machine, if not concerned by one of the rules bellow, will be silently dropped.
- Rule 1 : IRC. (Freenode) Those are the ports (from 6667 to 6697) that are necessary to connect to the Freenode IRC network and join the official #ubuntu-mate chatroom.
- Rule 2 : DNS. Important if you want to be able to translate domain names to address. (This is pretty much mandatory if you want to browse the web.)
- Rule 3 : HTTP(80) and HTTPS(443). Same thing: it's hard to browse the web without making outbound connections using those protocols.
- Rules 4+5 : SSH. A protocol to securely connect to machines on a network. I access a number of GNU/Linux machines remotely using the SSH client on port 22. The two way connection is necessary because I'm not always using the same machine to access other machines. If you're not the admin of more than one GNU/Linux machine you don't need this.
- Rule 6 : OpenVPN. I have a VPN running from my dedicated server, and it's by default listening on the UDP port 1194. If you don't use VPNs or if you use a different one (like Cisco VPNC) you don't need this.
- Rule 7 : NTP. Knowing the correct time can be useful.
- Rules 8+9+10+11 : E-mail. If you're using your web browser to access your email, you don't need to use the IMAP and SMTP protocols so you can snipe those rules. If you're using POP the port will probably be different too.
- Rules 12+13+14+15 : DHCP. To be able to get an IP address in my LAN, and therefore access to the Internet.
- The last rules (16+17+18+19) might be kind of weird to you. Those are actually not needed if you don't care what your kernel log file (/var/log/kern.log) looks like. The thing is I'm connected to a Massive LAN (Free WiFi access point for a residence / hotel where a lot of people live) that also happens to be massively hostile (loads of Windows machines around.) and the activity on the LAN generates a lot of multicast traffic that end up being logged to this file.
Lastly, and I'm afraid to say you can't correct that in the graphical interface, I've ran into a problem while attempting to ping a machine on the network.
If you don't need to ping machines on networks you don't need to do the following:
sudo nano /etc/ufw/before.rules
Then input the following after the section "# ok icmp code for FORWARD" :
# ok icmp code for OUTPUT
-A ufw-before-output -p icmp --icmp-type destination-unreachable -j ACCEPT
-A ufw-before-output -p icmp --icmp-type source-quench -j ACCEPT
-A ufw-before-output -p icmp --icmp-type time-exceeded -j ACCEPT
-A ufw-before-output -p icmp --icmp-type parameter-problem -j ACCEPT
-A ufw-before-output -p icmp --icmp-type echo-request -j ACCEPT
Then, save the file, exit the editor and run the command:
sudo service ufw restart
And you should be able to ping the net.
 sudo gedit ‘/etc/gufw/app_profiles/ubuntu-mate.profile’
sudo gedit ‘/etc/gufw/app_profiles/ubuntu-mate.profile’