For the last week or so, when I start my computer a mysterious request appears that a /bin/sh process requests root privileges and would I please authenticate. Not even for my best friend. A little investigation found this is coming from polkit-mate authentication-agent. Have I been hacked or is this legitimate. And, in any event, can I get rid of it or un-install it? This is my first post on a forum like this. Thanks for your help.
See: https://github.com/mate-desktop/mate-polkit. I think this is ok and welcome to the forum.
+--------------+
| App1 |
+--------------+
| libpolkit.so |<---------------+
+--------------+ |
|
+--------------+ V
| App2 | +------------+ +-----------------+
+--------------+ |--->| System Bus |<---->| polkit-backendd |
| libpolkit.so |<---| +------------+ +-----------------+
+--------------+ ^ | pk-backend-1.so |
| | ... |
+--------------+ | +-----------------+
| App3 | |
+--------------+ |
| libpolkit.so |<--------------
+--------------+
....Hey @bganton, good question and welcome to the forum! 


By itself, just because you've got a dialog box from Polkit doesn't mean you've been hacked. Polkit (formerly known as PolicyKit) is simply a mechanism on many Linux systems whereby an application that needs extra privileges to do something (install or update software, for instance) asks the Polkit daemon to carry out the privileged action. The Polkit daemon reads a set of configuration files to determine what to do; normally, the configuration files allow some things to be done without asking for your password -- such as mounting disks and USB flash drives that you attach to your computer -- while requiring you to give your go-ahead first for other things, such as formatting a disk, changing the system time, or installing software. The Polkit authentication agent is the program that actually asks you for your password; the authentication agent is usually not the program that wants more privileges.
Now, of course, there is a chance that the program asking Polkit for the privileges is malware (there's always a chance!), so let's find that out.
I'll give an example on my own system. I ran a program that needed more privileges to do its thing. Polkit presented me with this message:
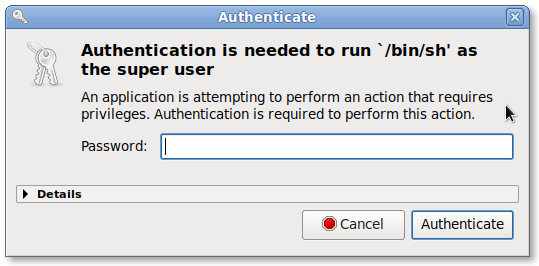
Well, that doesn't tell me much -- /bin/sh could be used to run just about anything! So let's open up that "Details" box at the bottom of the dialog (click on the "Details" string itself to open it):
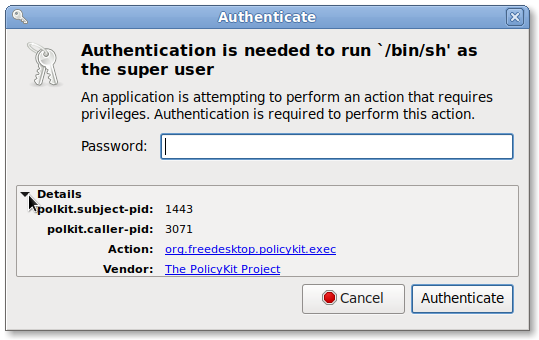
OK, two process IDs (PIDs) are listed in the details. The more important one here is the "caller PID", which is the PID of the program that requested the privileges from Polkit. Still, let's investigate both. Open a terminal window (you can press Ctrl-Alt-T to get one), then type:
ps -fp 1443
Of course, type in the appropriate PID that appears in your dialog! In my case, I got the following output:
UID PID PPID C STIME TTY TIME CMD
debian 1443 1438 0 19:49 pts/0 00:00:00 bash
This correctly shows that I ran the privilege-hungry program from another terminal window. That by itself doesn't tell us much, so let's try the next PID:
ps -fp 3071
I get this output:
UID PID PPID C STIME TTY TIME CMD
root 3071 1443 0 20:12 pts/0 00:00:00 pkexec /bin/sh -c evil commands
Well, in this case I obviously intentionally tried to run a bunch of evil commands, so not much of a shocker there. However, if you don't recognize either program, or you can't figure out what either program is doing asking for privileges, then post back here with the output of the ps command(s), and we'll tell you if it's safe or not!
I hope that helps! 