I cannot help but notice that on the download page (https://ubuntu-mate.org/wily/), all download links (both to the torrent files, to the iso files and to the MD5SUMS file) are plain http links, and https does not seem to be supported by the download server (cdimage.ubuntu.com). So, how are we supposed to make sure to have downloaded untampered files? Downloading the MD5 values via http from the same server as the payload makes verifying the hash value pointless (also, MD5 isn’t really safe to begin with).
Hi,
as long as you download the ISO from an official Ubuntu website, there shouldn’t be any reason to worry!.
I personally don’t use torrents as there is a possibility that someone will tamper with the files, that is just my personal preference and I have never read anywhere that someone had a tampered ISO using torrents!. 
Hi,
thank you very much. But I thought one cannot really trust http, regardless of the server (man-in-the-middle and such). Also, when the torrent file itself is tampered with, who knows what one is really downloading.
as long as you can see a lock symbol (green in this case) top left on the address bar, you should be safe, if in doubt, ask M.I.5, the CIA, NSA or BND!.
Right, the ubuntu-mate.org server offers SSL security (which is great!). But cdimage.ubuntu.com does not (which is not so great), and the download links go there. So even if the lock symbol is there on ubuntu-mate.org, once you click on the download link, you’re unprotected (I’m pretty confident the secret services you mentioned would agree with me). Malware attacks via tampered linux distros aren’t unheard of (http://blog.linuxmint.com/?p=2994), so this isn’t just unwarranted paranoia on my part. I think I’d rather not download Ubuntu for the time being, until such time as cdimage.ubuntu.com supports https. Thanks
The CD images on the Ubuntu servers are saved on Ubuntu’s own servers, the only way someone can tamper with a file is during the download and not on the server itself, Firefox has built-in security (afaik) so no one can tamper with the files during download!.
This is why I won’t use torrents because they can be tampered with!, I have downloaded countless images from Ubuntu’s servers over the years using https and have never had a problem!. 
I do agree with you that they could improve their security on the download site though!. 
Ok, thanks. I think I’ll try to reason with the webadmins of ubuntu.com, then. I cannot really fathom why they still offer such sensitive downloads without any form of security. If you ask me, that’s really dangerous, this day and age.
So long!
Actually, torrents are considered safe and harder to tamper with as each piece of the download is verified as it's downloaded. The peer-to-peer communication is how a torrent can get a clean piece if it was corrupt and the finished download can be verified using its hash.
The main difference is that it's giving back (uploading) to other users to avoid taking (leeching) and not giving back. It'll also save bandwidth costs for Canonical and Ubuntu MATE (if it's the Raspberry Pi downloads or Trusty 14.04) and sometimes achieve higher download speeds too.
@nizwiz, HTTPS security isn't strictly the solution. Checksums are common to verify the download is exactly how it was on the server (providing nobody broke into the server and changed it).
There are utilities for Windows and Mac, or if on Linux/Ubuntu, these commands:
sha256sum /path/to/file.iso
sha1sum /path/to/file.iso
md5sum /path/to/file.iso
md5sum is considered a vulnerable algorithm, I believe.
Links to the hashes can be found on the download page. Once the download completes, you perform the checksum and look at the appropriate file on the server. (e.g. SHA256SUMS / MD5SUMS)
A new download page will appear in time for 16.04, which will offer details on verifying downloads are intact.
There is another way of using GPG signatures, but I'm not sure how that works.
@lah7: The problem with the hash files is, they are served via http not https, so the hash values could be hacked along with the ISO images. And since the torrent files are also served via http not https, they could be hacked as well - so you could be downloading a completely different iso file from malicious seeders, or am I mistaken? Without using https download links, you can never be sure that you are actually downloading files from where you think you are. If you ask me, at the very least the hash files should be served via https (or the hash values embedded in https://ubuntu-mate.org/wily/), and SHA256 or better should be used for hashing.
That’s very true about HTTPS, and it’s possible that not all traffic is actually secure while in transit. CloudFlare’s “Flexible SSL” is an example of that, and gives a false sense of security on websites that use it:
-
Browser (HTTPS) ←
 → CloudFlare ←[unencrypted]-→ Server
→ CloudFlare ←[unencrypted]-→ Server
But thankfully many are:
-
Browser (HTTPS) ←
 → CloudFlare ←
→ CloudFlare ←  → Server
→ Server
– or – -
Browser (HTTPS) ←
 → Server
→ Server
You could go as far as saying you must be absolutely certain nobody broke into Canonical’s servers and replaced the files, HTTPS and hashes wouldn’t stop it either, but comparing hashes with community members via IRC or forums would indicate a problem.
The most secure way is to check a GPG signature:
A digitally signed file (like SHA256SUMS.gpg) is immediately invalidated if tampered with. This can only be signed with the private key (secret) along with a public key (which we can see).
This is the reverse of what I said, torrents okay, main server not!. 
@lah7: Well, the danger of the servers being hacked is always there. Still, that doesn’t mean that one shouldn’t try and preclude other attack vectors. Also, I would assume man-in-the-middle attacks are easier than hacking into the Ubuntu servers (I kinda expect a company like Canonical to have some talented security pros hardening their servers and making sure there are no unprotected connections behind the scenes, should they employ something like CloudFlare). So not serving downloads via https just unnecessarily makes life easier for hackers.
GPG seems to offer the best security, cumbersome as it is. I think I shall try and go that way, having no other options. Thanks for the link to the VerifyIsoHowto. If I may, I’d suggest to include that link and links to the appropriate SHA256SUMS and SHA256SUMS.gpg files on https://ubuntu-mate.org/wily/.
I still think the files should be served via https because - let’s face it - Ubuntu is the linux distro most entry-level linux users (such as myself) choose, many of them not being very tech-savvy, security-minded and willing to bother with verifying ISO images the right way (verifying a signature with trusted keys). They shouldn’t be left vulnerable to hackers sitting between the download servers and themselves. But I shall take that up with the guys at ubuntu.com.
Is it possible to include this information on the actual ‘Download’ page in a more simplified language so that those new to Ubuntu Mate (like me) know how to verify their downloads? Or better still to include utilities in the software boutique (if there are any?)
Are there any utilities to check and verify the MD5 and SHA-1 values of a file that could be included in the software boutique?
Hi
You mean some kind of GUI to implement the official procedure described @ https://help.ubuntu.com/community/VerifyIsoHowto ?
Yes, exactly. I am new to Linux and this procedure looks very complicated. Is there an easy way to do this through a GUI? I think on Windows there are several programs to do that. It would be great to have a suitable program included in the Software Boutique.
There’s a new help page on the recently updated Download page. See [How to verify downloads] (https://ubuntu-mate.org/how-to-verify-downloads) under the Direct Download section. There’s also some suggested GUIs if on Windows or Mac.
I’m not aware of any GUI apps for Ubuntu, but on Ubuntu (and most Linux systems), the sha256sum command is a terminal away. Or someone could create a Caja script.
K3b is a burning tool built for kubuntu and can auto generate md5 checksum. Maybe this would due.
http://www.mepis.org/docs/en/index.php?title=Checking_the_integrity_of_a_Live_CD
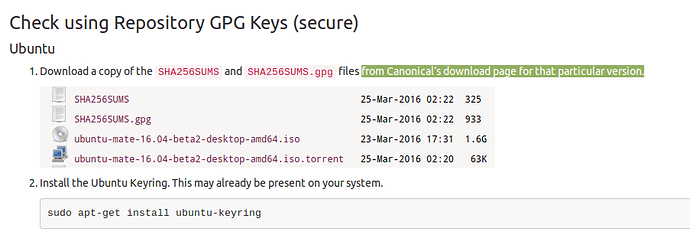
It would be great if an easy to use GUI tool to verify downloaded files is installed by default (or at least as part of the Software Boutique or a future security and privacy manager in the control center) in future Ubuntu MATE versions. The utilities mentioned so far are either not intuitive enough to use or not comprehensive enough. The new Download page is much clearer than in the past but not clear enough. I want to check the repository GPG keys but cannot find Canonical's download page. Is it possible to include a link on the UM Download page? A short description how the two verification methods differ would be beneficial as well.
 It could be as simple as a Caja script, like this:
It could be as simple as a Caja script, like this:
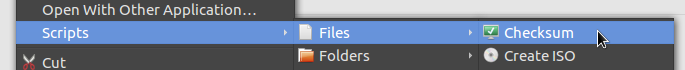
Thanks for pointing the missing details about the download page. I pushed out an amendment.